Containers attacks - ways of escape container

This post is I’m talking about container security topic , it’s demonstrate how a vulnerable application in dockerize environment can be critical catastrophic to enterprises.
Introduction Container technology has radically changed the way that applications are being developed and deployed. Notably, containers dramatically ease dependency management, so shipping new features or code is faster than ever before. While Docker containers and Kubernetes are great for DevOps, they also present new security challenges that both security practitioners and developers must understand and address with diligence.
Istio Security (securing microservices traffic with istio)
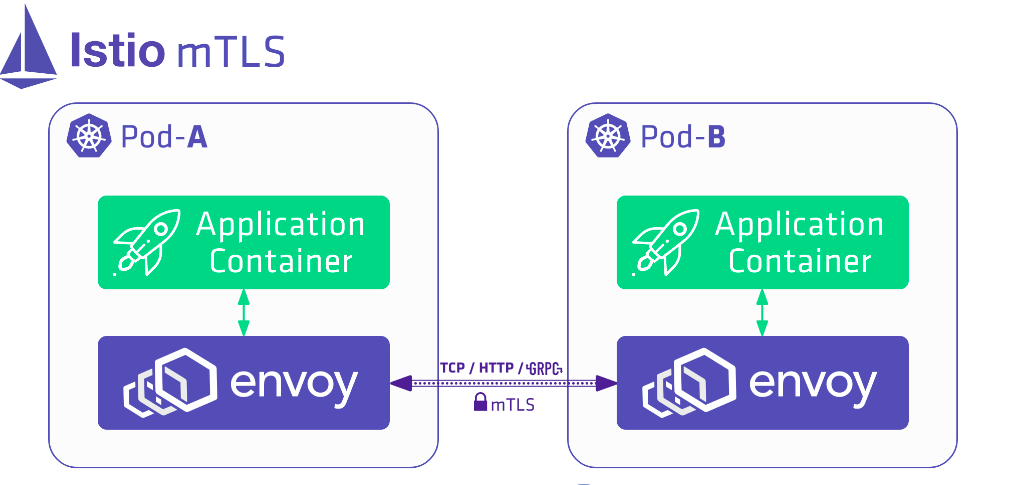
In this post I’m gonna talking about how to secure your micro-services in service mesh using istio. Prefer if the reader have a foundation knowledge of kubernetes but it’s not mandatory at all.
So What is Istio ? Istio is a service mesh that allows organizations to connect, secure and observe microservices. Since its inception three years ago, it’s risen to become one of Google’s most prominent open source projects, a top-three keyword at KubeCon, and a mature, production-ready offering supported by a robust community.
Browny Machine Writeup (easy)

======================
Hey guys , today I will walkthrough step by step in Browny Machine. this Machine is so good for beginner in pentration testing you will gonna learn a lot in this experenice. It is an easy linux machine , We will exploit Xplico Remote Code Execution in a vulnerable version Xplico that listen on port 9876 by default. There is a hidden end-point at inside of the Xplico that allow anyone to create a new user that can execute a terminal command under the context of the root user.